Martin Fowler
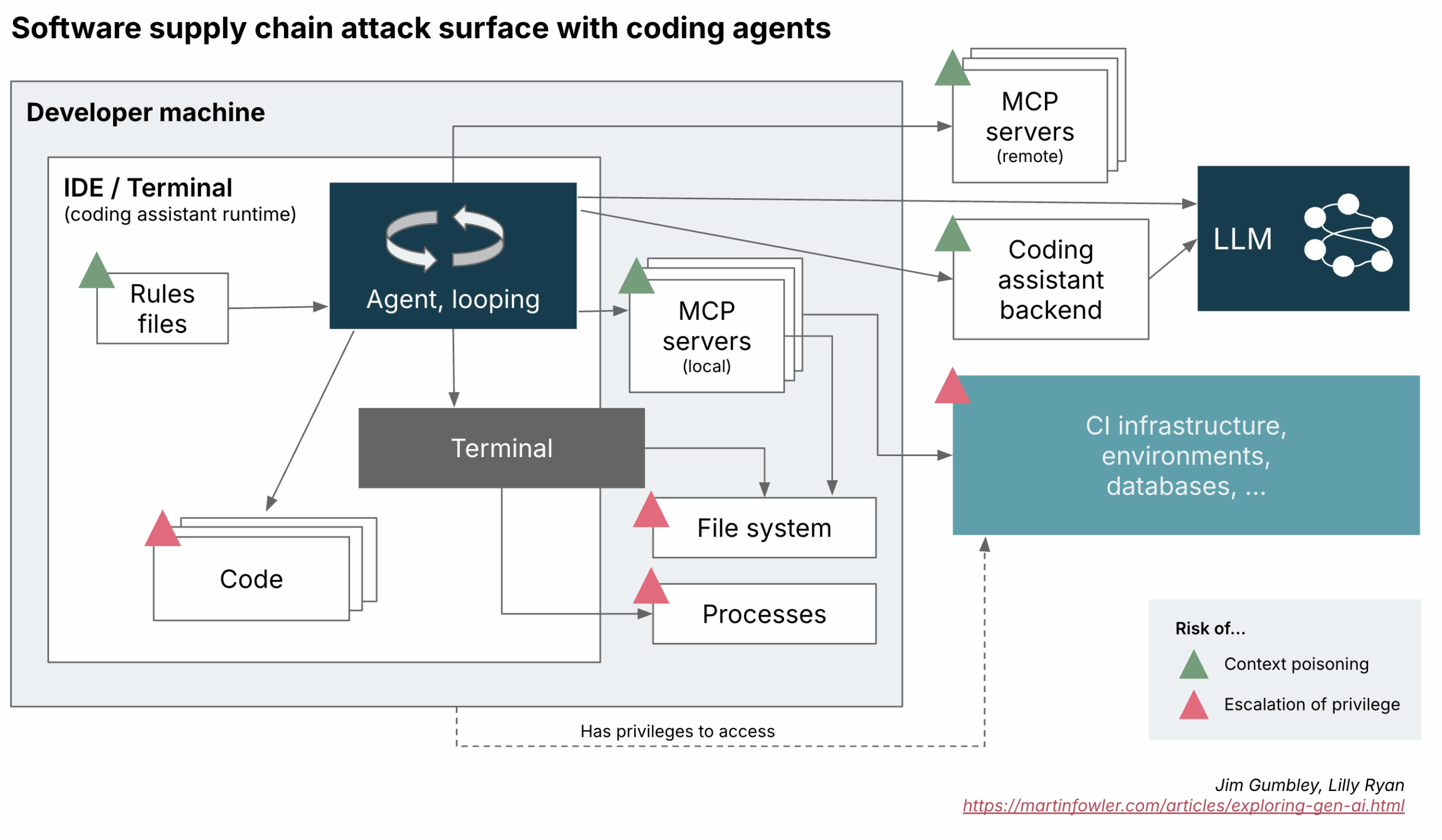
We have long recognized that developer environments represent a weak point in the software supply chain. Developers, by necessity, operate with elevated privileges and a lot of freedom, integrating diverse components directly into production systems. As a result, any malicious code introduced at this stage can have a broad and significant impact radius particularly with sensitive data and services.
The introduction of agentic coding assistants (such as Cursor, Windsurf, Cline, and lately also GitHub Copilot) introduces new dimensions to this landscape. These tools operate not merely as suggestive code generators but actively interact with developer environments through tool-use and Reasoning-Action (ReAct) loops. Coding assistants introduce new components and vulnerabilities to the software supply chain, but can also be owned or compromised themselves in novel and intriguing ways.
Understanding the Agent Loop Attack Surface
A compromised MCP server, rules file or even a code or dependency has the scope to
To read the full article click on the 'post' link at the top.