Martin Fowler
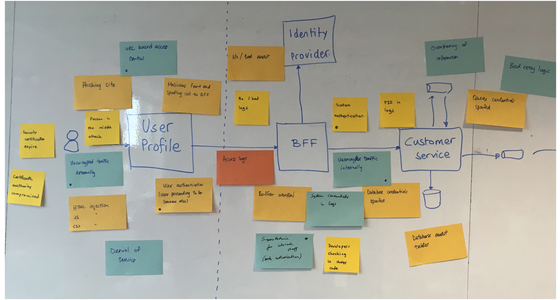
A worked example: Scope in the backlog
When they voted, the team decided that three threats were the most risky- and worthy of fixes.
Authorisation bypass direct to API
Although the user has to be logged in to see the page (is authenticated), the team realised there is nothing to stop unauthenicated requests direct to the API. This would have been a pretty major flaw if it had made it into production! The team had not spotted it before the session.
They added the following acceptance criteria to the story so it can be tested explicitly as part of story sign-off.
GIVEN an API request from the single page app to the API
WHEN there is no valid authorisation token for the current user included in the request
THEN the API request is rejected as unauthorised
XSS or injection via user input
The user profile feature allows user
To read the full article click on the 'post' link at the top.